Fundamentals of Internet DNS and DNS Record Types
Contents
- 1 DNS Fundamentals
- 1.1 How a DNS record gets updated
- 1.2 Domain Name System
- 1.3 What are DNS record types?
- 1.4 DNS record types
- 1.5 List of Online Tools for DNS propagation Check are as follows
- 1.6 What are DNS redirects?
- 1.7 How does DNS redirect work?
- 1.8 Types of DNS redirects
- 1.9 DNS redirect security concerns
- 1.10 Protection against DNS hijacking
- 1.11 What is DNS security?
- 1.12 Why is DNS security important and is DNS a security risk?
- 1.13 Authoritative and recursive DNS
- 1.14 Common DNS attacks
- 1.15 What is DNSSEC?
- 1.16 How to prevent a DNS attack
- 1.17 Conclusion
DNS Fundamentals
DNS is a service that turns your human-friendly domain name into a machine-friendly IP address of a server that can service your request. Every time you type in google.com or facebook.com as a URL in the browser, you’re essentially asking a DNS server where exactly the requested website is located. These requests run over UDP (the user datagram protocol). It’s a faster and more lightweight protocol than transmission control protocol (TCP). When you open your web browser to visit any URL, your computer will do one of these two things:
- If you’ve visited the website before, the computer will use cached DNS records.
- If you’re a first-time visitor, the recursive DNS server of your ISP will use a recursive query to find an IP address for the entered domain. It’ll do this by checking its zone file in the root servers or TLD servers.
How a DNS record gets updated
To understand how this works, let’s use an example. Let’s say you have an external DNS server at 10.0.1.5. It manages the domain example.com. But for some reason, this IP address changes to 10.0.1.6. (Perhaps a new VLAN, or virtual local area network, was created with an updated IP range.)
The external DNS that managed example.com would then send out a NOTIFY message to all of the other external DNS servers in the world that it knew. The DNS would tell them to update the IP address for example.com in their records.
Domain Name System
The domain name system, or DNS is a global system responsible for mapping human-readable hostnames to their corresponding internet Protocol addresses (IP Address). The human-readable hostname is a string of words that are easy to remember.
- IP Address (IPV4 32bit or 232=4,294,967,296 Addresses) on the other hand, written with Decimal numbers, has 4 groups each separated by dots and in each group there are three numbers (e.g 255.255.255.255) and are harder to remember.
- Similarly IPV6 Address (128 bit 2128 = 340,282,366,920,938,463,463,374,607,431,768,211,456 Addresses nearly unlimited) are written with hexadecimal digits. There are 10 numbers is the decimal numbering system. Beside, in Hexadecimal numbering system, there are 10 numbers and 6 letters (A, B, C, D, E, F). We can use both numbers and these letters (A, B, C, D, E, F) to create an IPv6 address. IPv6 address has 8 groups and each group is separated by colons. In each group, there are 4 digits (e.g. 2345:0425:2CA1:0000:0000:0567:5673:23b5). It is also harder to remember.
Also, note that the IP address associated with a domain name are volatile, it may change depending on the server hosting changes or moved to other hosting servers of particular hosted websites.
What are DNS record types?
DNS record types are records that provide important information about a hostname or domain. These records include the current IP address for a domain. Also, DNS records are stored in text files (zone files) on the authoritative DNS server. The content of a DNS record file is a string with special commands that the DNS server understands.
DNS record types
The following are the five major DNS record types:
- A record : The A record is the most important DNS record type. The “A” in A record stands for “address.” An A record shows the IP address for a specific hostname or domain. The main use of A record is for IP address lookup. Using an A record, a web browser is able to load a website using the domain name. As a result, we can access websites on the internet without knowing their IP addresses. Another use of A record is in the domain name system-based blackhole list (DNSBL). Here, the A record is used to block mail from known spam sources. Use @ to create the record at the root of the domain or enter a hostname to create it elsewhere. A records are for IPv4 addresses only and tell a request where your domain should direct to.
- AAAA record : AAAA record, just like A record, point to the IP address for a domain. However, this DNS record type is different in the sense that it points to IPV6 addresses. Usage of the AAAA record for DNS resolution has great potential because it uses IPV6, which is an improvement over IPV4. Also, as the internet keeps growing and we’re running out of IPV4 addresses, the potential for AAAA records is high. AAAA records are used to resolve a domain name to the newer IPV6 protocol address. Use @ to create the record at the root of the domain or enter a hostname to create it elsewhere. AAAA records are for IPv6 addresses only and tell a request where your domain should direct to.
- CNAME record : CNAME—or, in full, “canonical name”—is a DNS record that points a domain name (an alias) to another domain. In a CNAME record, the alias doesn’t point to an IP address. And the domain name that the alias points to is the canonical name. A practical example for the use of CNAME records is running multiple subdomains for different purposes on the same server. For example, we can use ftp.example.com for file transfer protocol (FTP) and serve webpages via www.example.com. We can then use a CNAME record to point both subdomains to example.com. The main domain example.com then points to the server’s IP address using an A record. It’s also possible to point a CNAME to another CNAME. However, doing so is inefficient and can lead to slow load speed and poor user experience. CNAME records act as an alias by mapping a hostname to another hostname.
- Nameserver (NS) record : A nameserver (NS) record specifies the authoritative DNS server for a domain. In other words, the NS record helps point to where internet applications like a web browser can find the IP address for a domain name. Usually, multiple nameservers are specified for a domain. For example, these could look like ns1.examplehostingprovider.com and ns2.examplehostingprovider.com.
- Mail exchange (MX) record : A mail exchange (MX) record, is a DNS record type that shows where emails for a domain should be routed to. In other words, an MX record makes it possible to direct emails to a mail server. You can have multiple MX records for a single domain name. And what this means is that you can have backup email servers. With an MX record, it’s possible to hand off emails to a dedicated email server. For example, you can decide to leave all the trouble of setting up webmail on a server you own to a specialized email provider. This comes with many benefits, including custom email clients for reading and sending emails, and improved security and spam filters. Also, you can use a service like Site24x7 to monitor and verify issues with the mail server your MX records point to. MX records specify the mail servers responsible for accepting emails on behalf of your domain, and priority value if your provider has a number of mail servers for contingency.
- SOA record: SOA stands for “start of authority.” It’s an important DNS record type that stores admin information about a domain. This information includes the email address of the admin and when the domain was last updated.
- TXT record: TXT stands for “text,” and this record type lets the owner of a domain store text values in the DNS. Several services use this record to verify ownership of a domain. TXT records are used to associate a string of text with a hostname. These are primarily used for verification.
- PTR record: A pointer (PTR) record provides a domain name for reverse lookup. It’s the opposite of an A record as it provides the domain name linked to an IP address instead of the IP address for a domain.
- SRV record: Using this DNS record type, it’s possible to store the IP address and port for specific services. SRV records specify the location (hostname and port number) of servers for specific services. You can use service records to direct certain types of traffic to particular servers.
- CERT record: This record type stores public keys certificates.
- CAA Record: CAA records specify which certificate authorities are permitted to issue certificates for a domain. Use them to reduce the risk of unintended certificate mis-issue.
- DCHID: This DNS record type stores information related to dynamic host configuration protocol (DHCP).
- DNAME: The full meaning of DNAME is “delegation name.” This record type works very similarly to CNAME; however, it points all the subdomains for the alias to the canonical domain name. That is, pointing the DNAME for secondsite.com to example.com will also apply to staff.secondsite.com and any other subdomain.
List of Online Tools for DNS propagation Check are as follows
https://mxtoolbox.com/ https://dnschecker.org/ https://www.whatsmydns.net/ https://dnsmap.io/ https://www.nslookup.io/ https://toolbox.googleapps.com/apps/dig/
What are DNS redirects?
DNS redirection is a feature many hosting companies and domain name registrars offer. You can use various methods to accomplish redirects, but DNS redirection is the simplest. A DNS redirect allows you to point one domain name to another, achieving the same result as if you had changed your original domain’s name servers.
How does DNS redirect work?
You can think of a DNS redirect as similar to looking up a book in a library card catalog. You find the right section, go there, and then look up the number corresponding to your desired book’s location on one of the shelves. The librarian then brings you over to the correct shelf and finds your book. It’s similar to what happens when you’re searching for a website over the internet.
For example, when you type www.google.com into your browser, it’s because you think Google should be located at that address. But the domain name isn’t enough information to figure out where Google actually is. Luckily, your browser contacts a DNS server and asks it where Google is located on the web—just like looking up a book in the library’s card catalog. The DNS server knows the exact address, so it makes your browser send requests to that location.
Types of DNS redirects
Now that you know what DNS redirection is and how it works, let’s learn about the various types of DNS redirects.
- CNAME Redirects: CNAME redirection is a type of DNS redirection where one domain name is mapped to another. For example, if you want to map the domain name www.example.com to the domain name www.otherdomain.com, you would create a CNAME record with the name “www” and the value “otherdomain.com”.
- URL Redirects: You can use URL redirection, or URL forwarding, to send web traffic to a different URL than initially requested. To set up URL forwarding, you can modify the DNS record for a domain name to point to a different web address. When users visit the original URL, the DNS redirects to the new URL. There are two types of URL redirection: permanent and temporary.
- Permanent redirects (or 301 Redirects): If you permanently moved a web address or URL traffic to another address, you would set up a permanent redirect. Also called a 301 redirect, it’s the most common type of URL redirect. For example, when a user types gmail.com in their browser but gets redirected to mail.google.com, that’s an HTTP 301 redirect. Here, the web server sends a message to the browser that the page has permanently moved to a new location. The browser then updates its cache with the latest information and continues to use the new site in the future.
- Temporary redirects (or 302 Redirects): You would use temporary (or 302) redirection when you have moved the original page temporarily but plan to restore the original location sometime in the future. 302 redirection directs traffic from the original web address to a new one, but only temporarily. Users could come back later, and the redirect will have disappeared, essentially allowing users to reaccess the original site. Temporary redirects have a negative impact on search engine optimizations (SEOs), as search engines might treat the content of these webpages as duplicates.
- URL frame: Hackers use the URL frame technique to inject malicious code into a website. They insert the code into the website’s URL. When the victim visits the site, the code is executed. Hackers can use this technique to steal information or install malware on the victim’s computer.
- IP address redirects: Commonly, an IP address redirect masks the IP address of a server or device. IP address redirection allows many domains to exist on one IP address. This makes it more difficult for hackers to know where all your websites are on the internet. Often, website owners use IP address redirection so they can use one IP address for multiple domain names. Web admins welcome these redirects because it saves them money and takes some pressure off their servers.
- Meta refresh: Finally, the last type of DNS redirection is a meta refresh redirect. This type of redirect sends traffic from one address to another using an HTML tag. A developer inserts meta refresh code into the HTML header of the website. The code then tells the web browser to refresh the page after a set amount of time. Meta refresh redirects send users to a new page without having to type the new URL into their web browser. It can be helpful if you change your website’s design or layout and you want your users to see the latest changes as soon as possible. Below is an example of the HTML code snippet you would use to achieve a meta refresh redirect:
<meta http-equiv=”refresh” content=”5; url=https://www.anotherdomain.com”>
Here, the browser will be redirected to https://www.anotherdomain.com after five seconds. It’s useful for certain types of navigation menus and other time-sensitive tasks.
DNS redirect security concerns
Below are some security threats related to DNS redirection that you must be aware of.
- DNS hijacking: Domain name registration can be easy to obtain; hackers can use automated scripts to search for unregistered domains that may be similar to well-known sites. Once they find an unregistered domain with a common typo, they can purchase it and set up their site for phishing purposes. For example, if you typed “fakebook” instead of “facebook” in your web browser address bar, you would end up at a compromised website that looks like the actual website and asks you to enter your login credentials.
- DNS cache poisoning: In DNS cache poisoning, an attacker injects illegitimate data into the DNS cache. This causes the server to return the wrong information for a specific domain name. Hackers can use it to redirect users to a malicious website or steal data.
- Exploiting vulnerabilities in routers: An attacker can change the client’s configuration to point to an alternative nameserver or IP address. For example, routers have a built-in nameserver that clients query before going to their default ISP’s nameservers. By exploiting a vulnerability on a router, attackers can then change the configuration that the client queries first.
- DNS spoofing: In DNS spoofing, an attacker sends a fake DNS response to a victim’s computer. This causes the victim’s computer to believe that the malicious website is a legitimate one.
- Man-in-the-Middle attack: A man-in-the-middle attack is when an attacker intercepts and manipulates traffic between the victim’s computer and the DNS server.
- Invalid record deletion: An attacker may delete legitimate DNS records, preventing a computer from receiving the proper IP address for a specific domain name.
Protection against DNS hijacking
The best way to protect yourself against DNS hijacking is by using Domain Name System Security Extensions (DNSSEC). This suite provides authentication for DNS responses, meaning that the authenticity of every response packet is cryptographically signed by the authority that sent it. DNSSEC ensures that clients receive a correct response from the queried domain and not a spoofed one. However, DNSSEC has been around since 2008, and many ISPs are yet to implement it into their DNS servers despite its availability.
ISP DNS servers currently don’t have a feature that warns users when they have been redirected to a malicious IP. To protect yourself from DNS hijacking, it’s also essential to check the authenticity of your DNS server’s responses. The simplest way is by comparing what you expect a domain to be with your ISP’s DNS response for that same domain. If these two values don’t match, the DNS server’s response has been spoofed.
For example, look up for the domain brsmedia.in on your ISP’s DNS server by using the dig command in Debian 11 Operating System:
$ dig brsmedia.in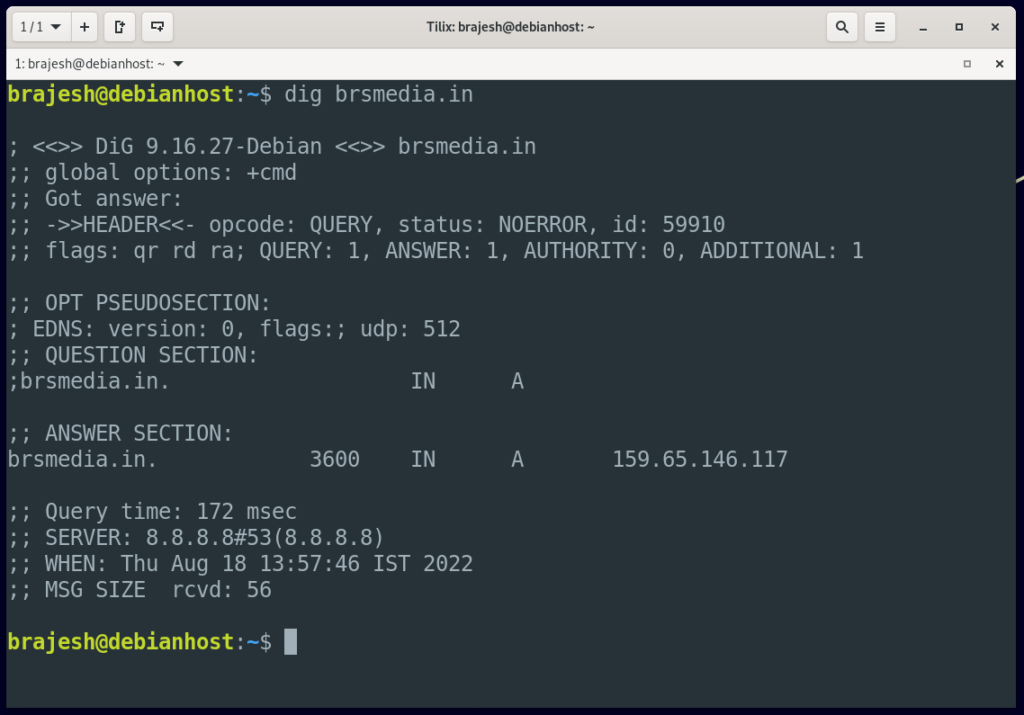
And then look up brsmedia.in on Google’s DNS server, by using the command:
$ dig google.com @8.8.8.8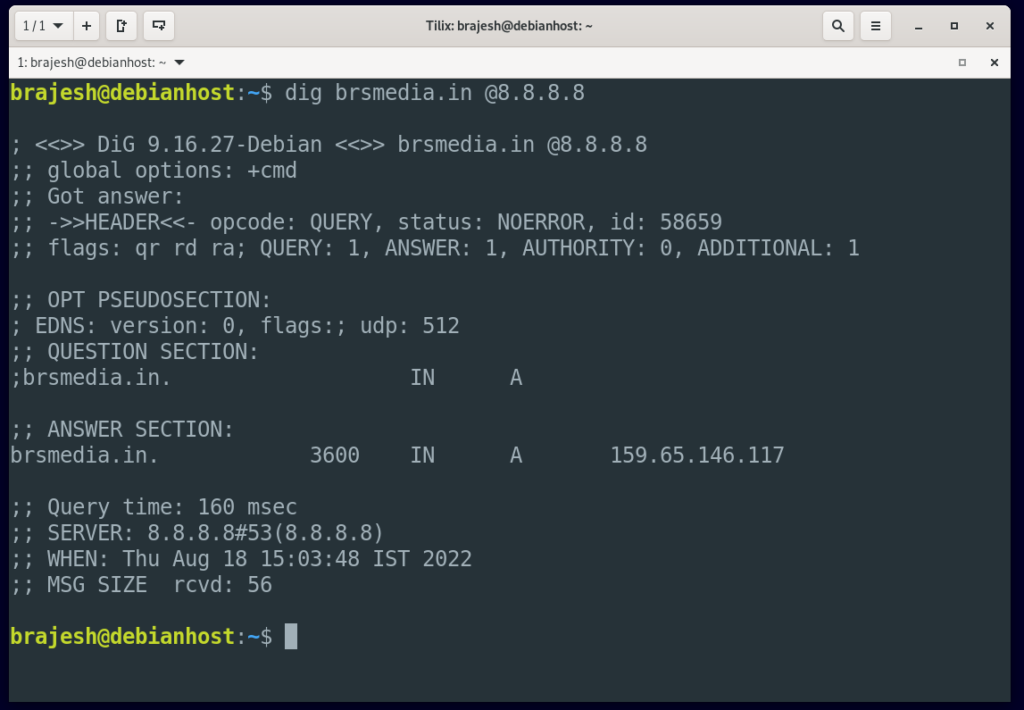
The results of these two commands should be the same. If they’re not, then your ISP’s DNS server has been spoofed.
Note: While DNSSEC is a handy security measure to protect your computer from attacks, it is not foolproof. There are still ways that an attacker could redirect your queries and make you think everything was fine. For example, they could redirect non-critical domains like bing.com and then have their malicious servers respond to critical requests like passwordreset.microsoftonline.com.
What is DNS security?
DNS security is the protection and prevention of the domain name system against vulnerability and attacks by cybercriminals.
Why is DNS security important and is DNS a security risk?
When the internet was first created, it was mostly used for communication by a small number of people (e.g., the military and universities). But as popularity grew, more people began to use the internet for personal use. Because people can’t readily memorize IP addresses, there was a need for an intuitive way to solve the problem. As a result, DNS was born. Its purpose was to make it simple to access the internet by supplying domain names that were mapped to their associated IP addresses.
When DNS protocol was created, little attention was paid to its security, which allowed the DNS traffic to move freely through network firewalls. By taking advantage of this vulnerability, malicious actors can create fake DNS records that lead users to fake websites or make them perform malicious actions. As a result, DNS security is an important focus.
Authoritative and recursive DNS
To better understand what authoritative and recursive DNS are, let’s look at this scenario.
Let’s say you want to access a website using a domain name on your web browser. There is a resolver on your device (called stub resolver) that checks its database to know if it has the requested domain. If the requested domain is not in its record, the stub resolver sends a query to another resolver on the internet called the recursive resolver (or caching nameserver).
A recursive resolver is a nameserver usually provided by an internet service provider or other service providers, such as Google. It first checks its cache to know if it has the domain name in question. If it doesn’t, it then sends a query on behalf of the user program (web browser) to an authoritative nameserver to obtain the IP address of the requested domain. It then returns the address to the user.
An authoritative nameserver is a system that takes a domain name and responds with information about the resources in that zone. It is where the IP address and the domain name of a particular website are located.
Common DNS attacks
- Denial of Service (DoS) attack: In a DoS attack, malicious actors overload an authoritative server with an excessive number of queries, making it impossible to use the server. The server then crashes because it is unable to respond to all of the queries. As a result, other users or servers that want to access that server will be denied the service.
- Distributed DoS (DDoS) attack: DDoS is a more elaborate form of DoS. It involves using multiple systems to overload the targeted server with excessive queries. The malicious actor employs tens of thousands of computers to perform the task.There are two main DDoS attack methodologies: amplification and reflection.
- DNS Amplification: DNS amplification is a DDoS attack in which the attacker uses DNS server weaknesses to transform minor queries into much bigger payloads. The attacker then uses this increased traffic to bring the victim’s servers down. It is done by flooding the server with short requests/queries that in turn will return large responses (e.g., querying for a Txt file on a DNS server).
- DNS Reflection: Reflection DDoS attacks are attacks that use the same protocol in both directions. The attacker spoofs the victim’s IP address and uses User Datagram protocol (UDP) to submit a request for information to servers that are known to respond to such requests. The server receives the message, then sends a response to the victim’s IP address. The victim, according to the servers, was the one who made the initial request. All of the information from those servers accumulate, clogging the target’s internet connection.
- Cache poisoning or data spoofing: Cache poisoning, also known as data spoofing, is the process whereby a malicious actor injects a fake DNS entry into a DNS server. As a result, the user is sent to illicit resources (e.g., fake websites). Take, for example, a user who wants to access their financial websites. On the other side, an attacker has changed the DNS server so that when a user enters a domain name, they are redirected to the attacker’s phony replica of the banking website. The attackers can then steal valuable information by prompting the user to input their credentials on the bogus websites.
- Fast Flux: Attackers use Fast Flux to conceal their identity by using rapidly changing sensitive information to hide the source of the attack. It comes in two forms: single flux (which includes changing IP addresses simultaneously) and double flux (which involves constantly changing IP addresses and domain names).
What is DNSSEC?
Because DNS data is intended to be public and distributed over the internet, it is important to protect the data’s confidentiality. Integrity, source authentication, and availability are the three main security goals for DNS.
DNSSEC is a series of extensions designed by the Internet Engineering Task Force to secure data exchange in the DNS. DNSSEC ensures the authenticity and integrity of DNS data by preventing applications from receiving forged or false DNS data. It works by using digital signatures to encrypt DNS data. The recursive resolver can tell if the information received from the authoritative server is authenticated by inspecting the digital signature.
The DNSSEC functions in this way: Each DNS zone has its own set of private and public keys. The zone owner signs the data with the private key and creates a digital signature over it. Any recursive resolver that wants to access the data will also need to know the public key to validate the data’s authenticity. The recursive resolvers then authenticate the digital signature’s validity before returning the DNS data to the user. The recursive resolvers reject the data if the signature does not validate, and then return an error to the user.
How to prevent a DNS attack
- Configure your DNS to be as secure as possible. You can do this by using a random port instead of the standard port for DNS (i.e., UDP port 53). You can also achieve this by randomizing the query ID and the case letters of the domain names that need to be resolved.
- Add more security to recursive DNS servers. By using access control such as DNS filtering (the technique ISP uses to prevent its network from online threats), DNSSEC, and other means, you can safeguard the recursive server from unauthorized access.
- Keep your resolver safe and secure. Don’t expose resolvers to the public; instead, limit them to the users using the network. This will prevent malicious actors from spoofing (altering) the nameserver.
- Integrate DNSSEC into your operations to validate the integrity of your data. DNSSEC improves the security of DNS protocol, preventing applications from receiving forged or false DNS data.
- Keep your DNS servers up to date. If you are using third party DNS servers for your operations ( like Google DNS, Cloudflare), you won’t need to worry about updating the DNS server. If you run your own nameserver, however, you’ll need to update it from time to time to get new security features and improve the performance of your DNS operations.
- Enable DNS filtering. DNS filtering is a way to isolate a user from malicious websites. It allows a system administrator to block users from sites that are known to contain malicious information. If a user wants to access that site, the DNS server disconnects all communication immediately.
Conclusion
DNS redirects are a way of altering the DNS information associated with a domain name. You can use it for various purposes, including security, load balancing, and marketing, as it can direct users to different webpages. Understanding how DNS redirects work can help you protect your computer and data from malicious users, as well as preventing malware attacks and frauds.
Furthermore: Practical Implementation of DNS and Firewall security in Home and Enterprise network will be published soon.
Key Terms:
- CoreDNS ,
- DNS Configuration ,
- Enforce Secure DNS ,
- Firewall ,
- Open Source Software ,
- OPNSense ,
- pfsense ,
- pihole